Service Overview
LANSCOPE on GIO provides LANSCOPE as a SaaS to provide subscribers with IT asset management, internal fraud prevention, and external threat protection functions on client PCs they own.
It includes LANSCOPE administrative servers (the manager) on the IIJ GIO Cloud for subscribers, so they do not need to install or maintain the manager themselves, allowing them to keep initial expenditures and operating costs down.
The service also manages client PCs subscribers own.
By installing the LANSCOPE Integrated Console (the management console) on system administrators' PCs, subscribers can create and edit rules and policies for managing client PCs on their networks. *“Client PCs” refers to servers, PCs, and portable notebook PCs on subscriber networks.
-
Client PCs” refers to servers, PCs, and portable notebook PCs on subscriber networks.
Structural Diagram
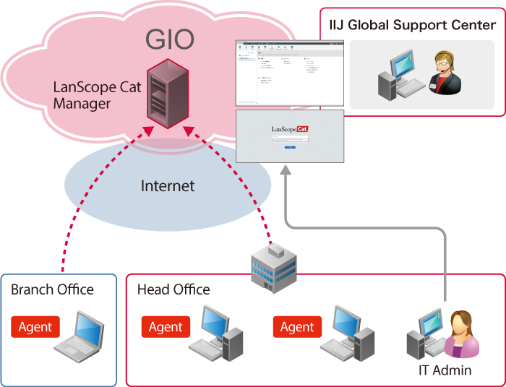
-
Client PCs and our service facilities remain connected via the Internet.
-
Subscribers do not need to use IIJ services for their Internet connections.
Service Highlights
Integrated security tools
A one-stop solution for IT asset management, internal fraud protection, and external threat countermeasures
Centralized management of multiple devices
Centralized management of multiple devices, even outside of VPNs
Low cost
With no need for dedicated servers or server maintenance, endpoint management is possible with minimal setup time
In addition to IT asset management, LANSCOPE serves as an integrated security tool that protects endpoints from information leaks and malware infection risks.
LANSCOPE on GIO Service Features
Basic features
| Web console | Provides a web-based, at-a-glance console for past log searches and numerical values representing the current security status. |
|---|---|
| Network detection | Detects connections from unauthorized terminals, such as personal PCs, to the network. |
| IT asset management | Gathers and manages client PC asset information (including hardware, OS, and software installation information). |
| Software asset management | Helps create ledgers needed to manage licenses and other software assets. |
| App batch/automatic installation | Allows for automatic installations and batch distributions of files and applications. |
| Operational log management | Stores client PC operations (opening and closing files, running applications, printing documents, etc.) and their outcomes in logs for up to five years, and detects abnormal or fraudulent activity. |
Optional features
| Device control | Controls usage restrictions and prohibitions for CDs, DVDs, USB memory, and other devices for each client PC. Also allows administrators to configure permissions for specific USB devices or identify known USB devices. |
|---|---|
| Web access management | Records website browsing, loading, uploads, and downloads, and blocks these activities using blacklists. |
| Malware management | Uses BlackBerry’s AI engine BlackBerry Protect to detect and quarantine malware and track malware paths. |
Additional non-functional services
| Backup / version upgrade operation | IIJ will carry out regular backups and upgrade the system as necessary. |
|---|



