What is Secure Access Service?
Safous Zero Trust Access/ZTA, a secure access service allows you to safely and securely access important corporate resources anytime, from anywhere. The advanced authentication and authorization function helps you achieve optimal access control.
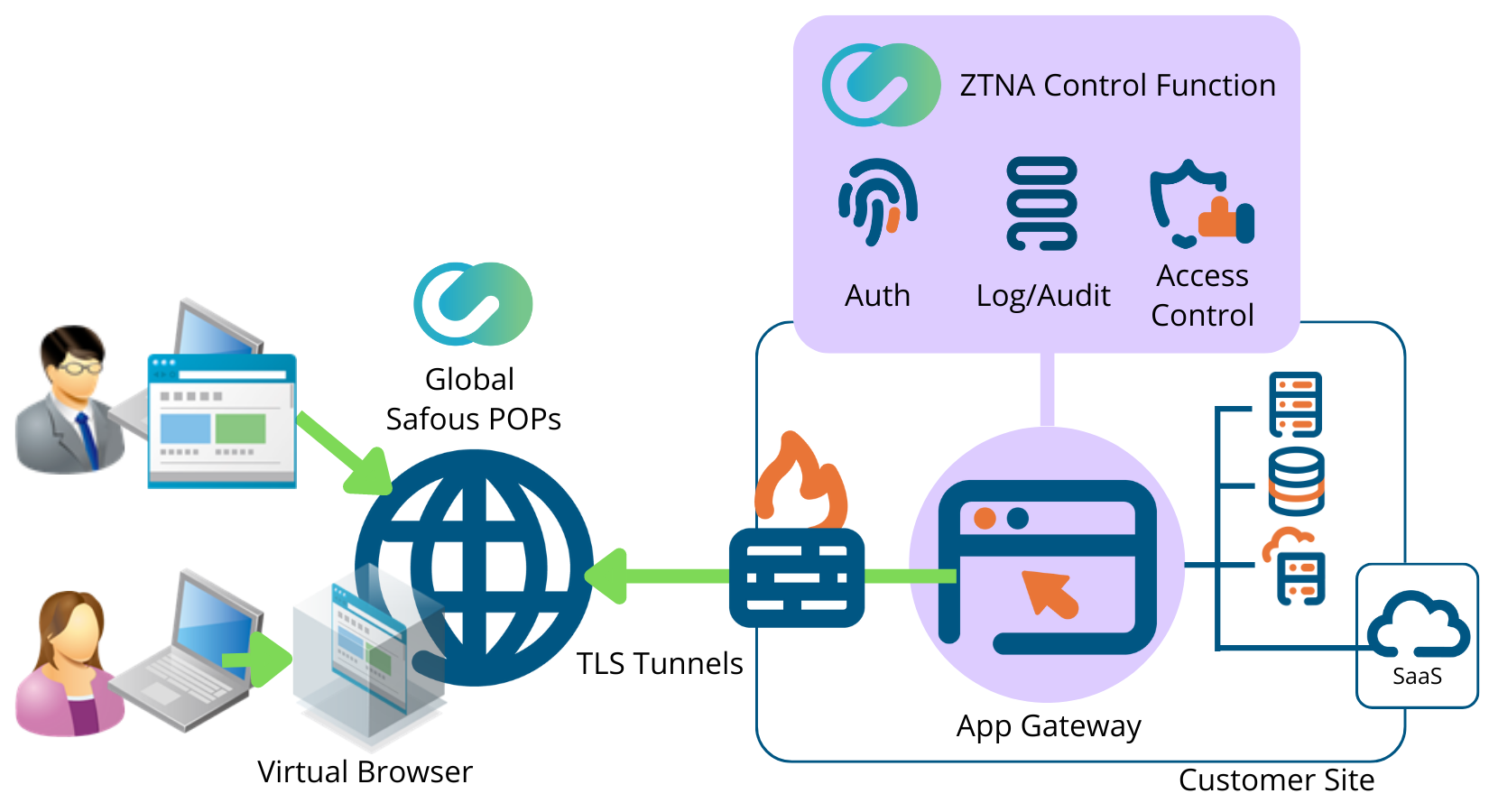
Zero Trust Network Access
The ZTNA architecture is a "software-defined policy-based architecture" that enables a new approach to internal application access. ZTNA eliminates the need for traditional network perimeters such as VPNs by connecting each user directly to authorized applications with granted policies.
This new architecture dramatically reduces a company's cyber risk and exposure to cyber threats. This means protecting your company's internal resources from network-level hacks and ransomware/malware attacks.
Keys of ZTNA
- MFA and flexible policy controls
- Connect users to applications, not networks
- Hide corporate resources from the internet
- Record all user activity
Service Features

Protect Enterprise Resources
Allows users to securely connect to resources within your premise or in the cloud. No agent Installation needed, users can access their resources as long as they have internet connection and a browser. With the Browser Isolation Function, users can separate application access and the device. This allows users to safely navigate the internet through their browser.

Advanced Authentication/Authorization
Safous provides application-based access and risk-based policy control, as well as Multi-Factor Authentication and Single Sign-on functions. Authorization is highly customizable, device credentials, location, time of access are just a few categories that can be applied to access control. This allows for privileged access management where users can only access resources they have permission to. Compatible with authentication systems as follows; AD/LDAP/SAML/OpenID.

Agentless Implementation
Safous provides application-based access and risk-based policy control with no agent needed. This allows any user, from any device, with any OS to access their online resources while maintaining maximum security.

GDPR Compliant
Safous does not store any customers' data in the cloud. Privacy data is always kept on the customer’s site allowing users to have full control over their data.
Highlight Functions
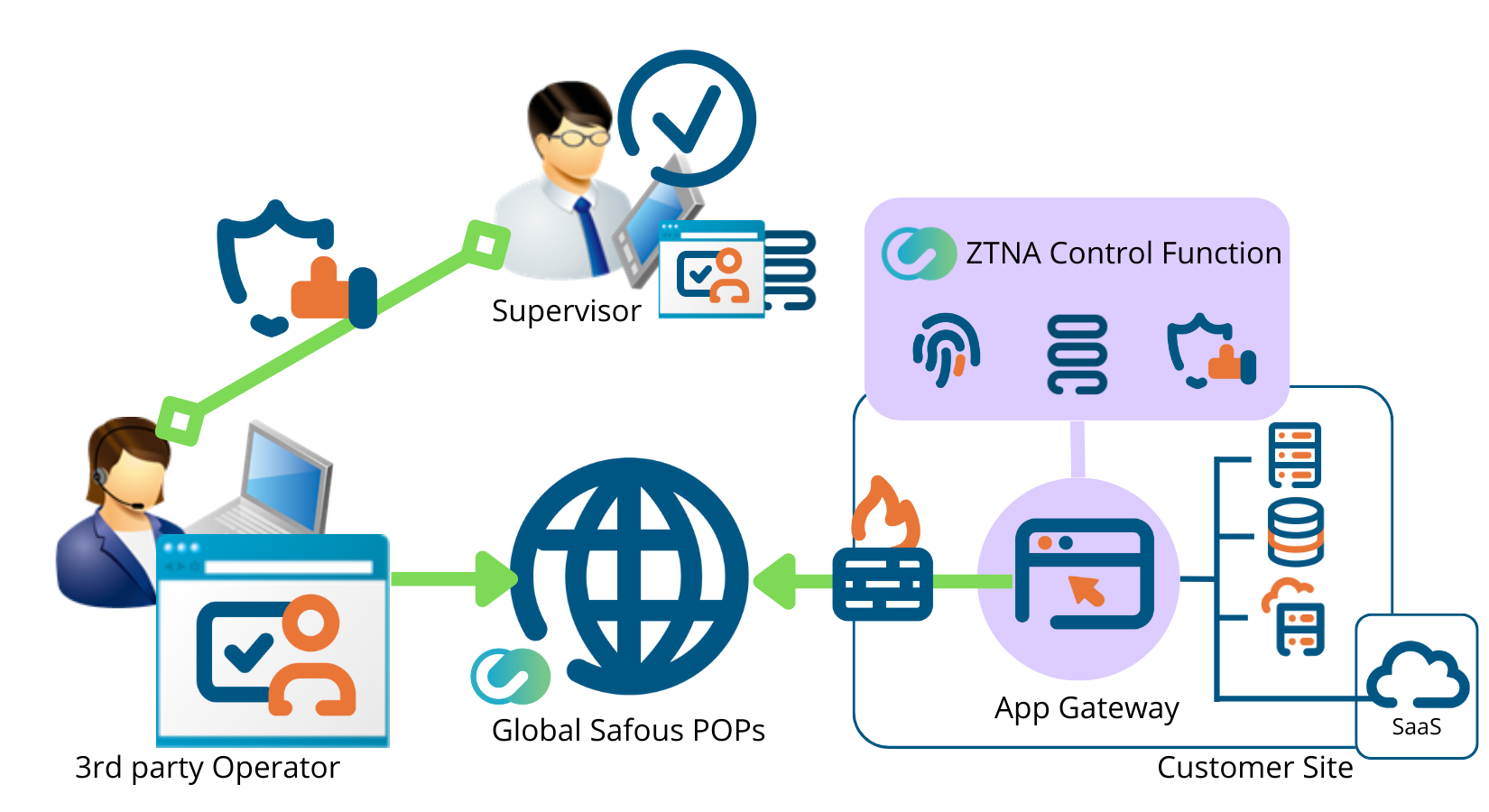
Supervised Access and Session Recording Functions
It has a supervisor function and a session recording function that are effective for third-party access management.
If the supervisor function is set for an individual user, when the user tries to log in, the login will not be allowed until the supervisor approves it. The user must wait in the waiting room until approved. After the user logs in, the supervisor can directly see the user's console by pressing the "Supervise" button. By using this function, supervisors can check the login status of a user who has a strong privilege (such as super admin) and the activities in real time. Moreover, supervisors can interrupt into the sessions, so that third-party access can be watched. Additionally, you can record the entire session.
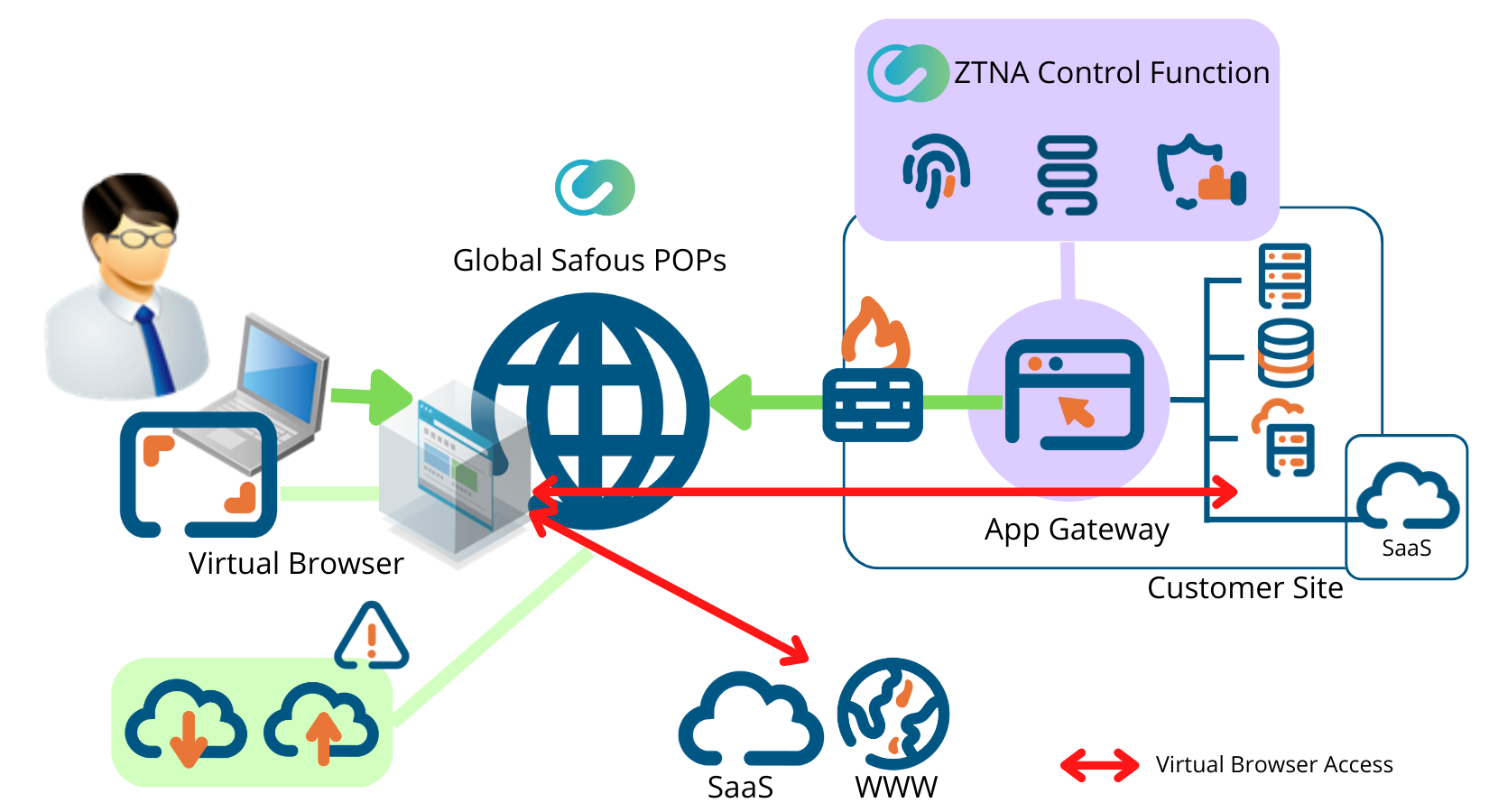
Browser Isolation Function
Safous Browser Isolation Function will provide a sandbox-type virtual browser on one of Safous’ access points. (PoP: Point of Presence) Establishing access through this virtual browser will allow users to navigate the web without risking their devices.
This is made possible through Safous’ ability to completely separate the end device from the Web. By doing so, even in the case, there are vulnerabilities on the device, attackers will not be able to intrude and exploit it. Safous’s Browser Isolation can be utilized for Data Loss Prevention(DLP) as well. By restricting file uploads and downloads, users can restrict which confidential information can be uploaded to the public, allowing organizations to better protect their resources.
Service Type
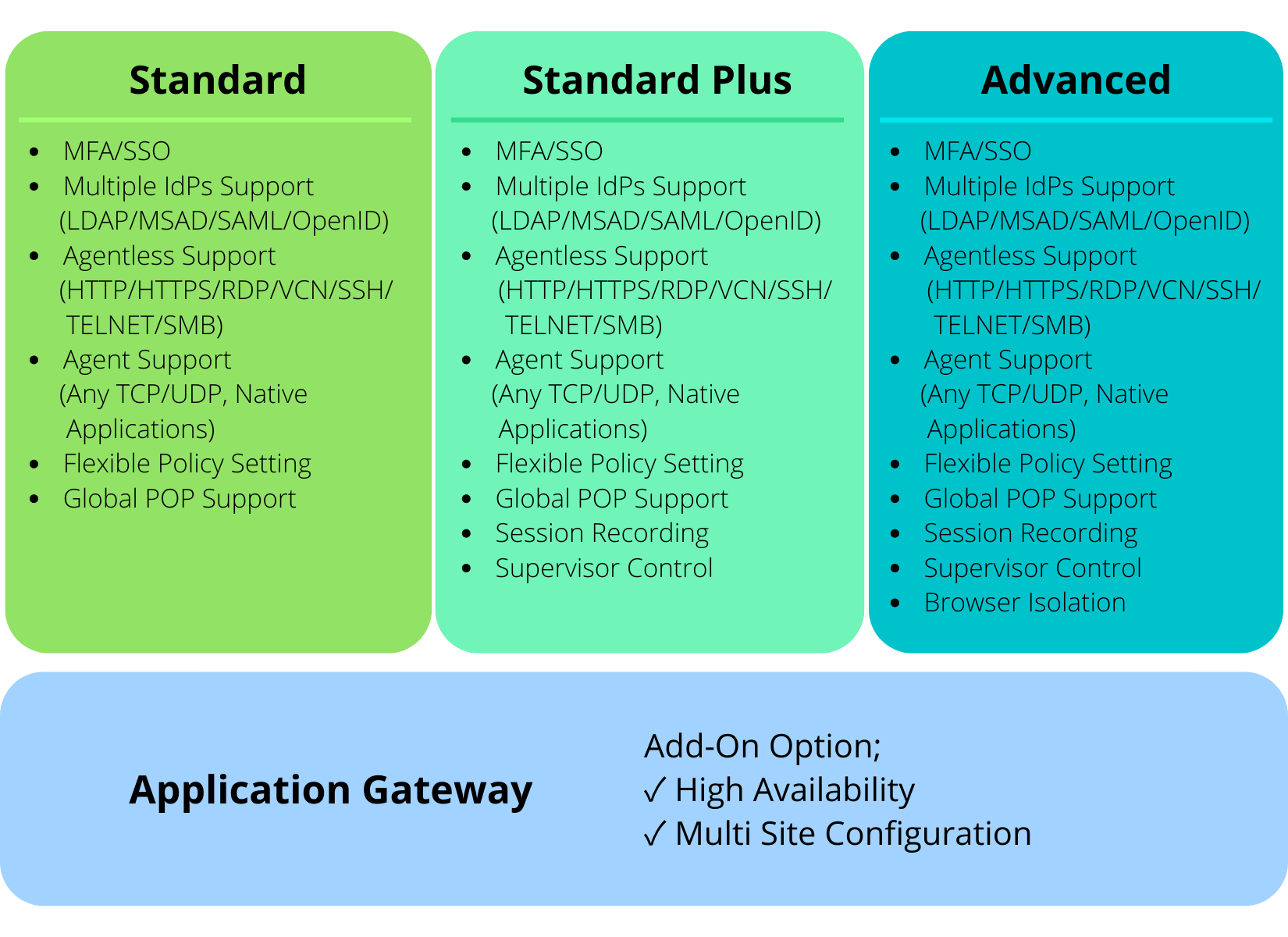
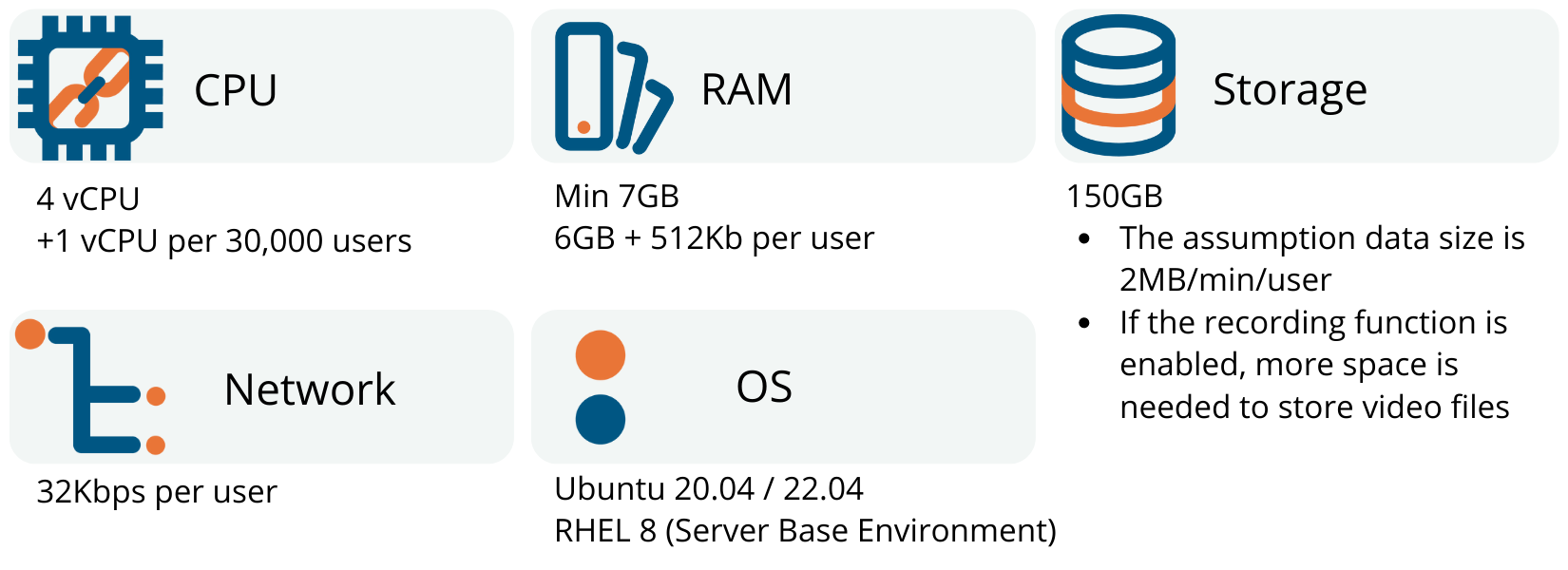
Application Gateway Specification
Safous will provide an application gateway software to be installed on a server in the customer's environment. The server specifications required for building an application gateway are as follows.
Use Cases
Here are some application examples of services that leverage the strengths of zero trust network access.

Access control at tenants
You can set up multiple users on a single device at locations with limited resources. Through a browser, multiple users can safely and securely access each users' permitted applications. Grant Zero Trust access or temporary policy to 3rd party collaborators or consultants can be managed easily.

MFA for a legacy system
Enable Multi-factor Authentication for all of your internal resources, even for legacy systems and embedded systems that cannot (or do not) support multi-factor authentication.

Additional ZTNA layer
By adding a ZTNA control layer to your existing environment, you can implement a zero-trust access environment for your remote access users and LAN users. With Safous, users will access their business resources the same way, whether they are at an office, at home, or at a coffee shop, all access to business resources will be routed through the Safous PoP.




